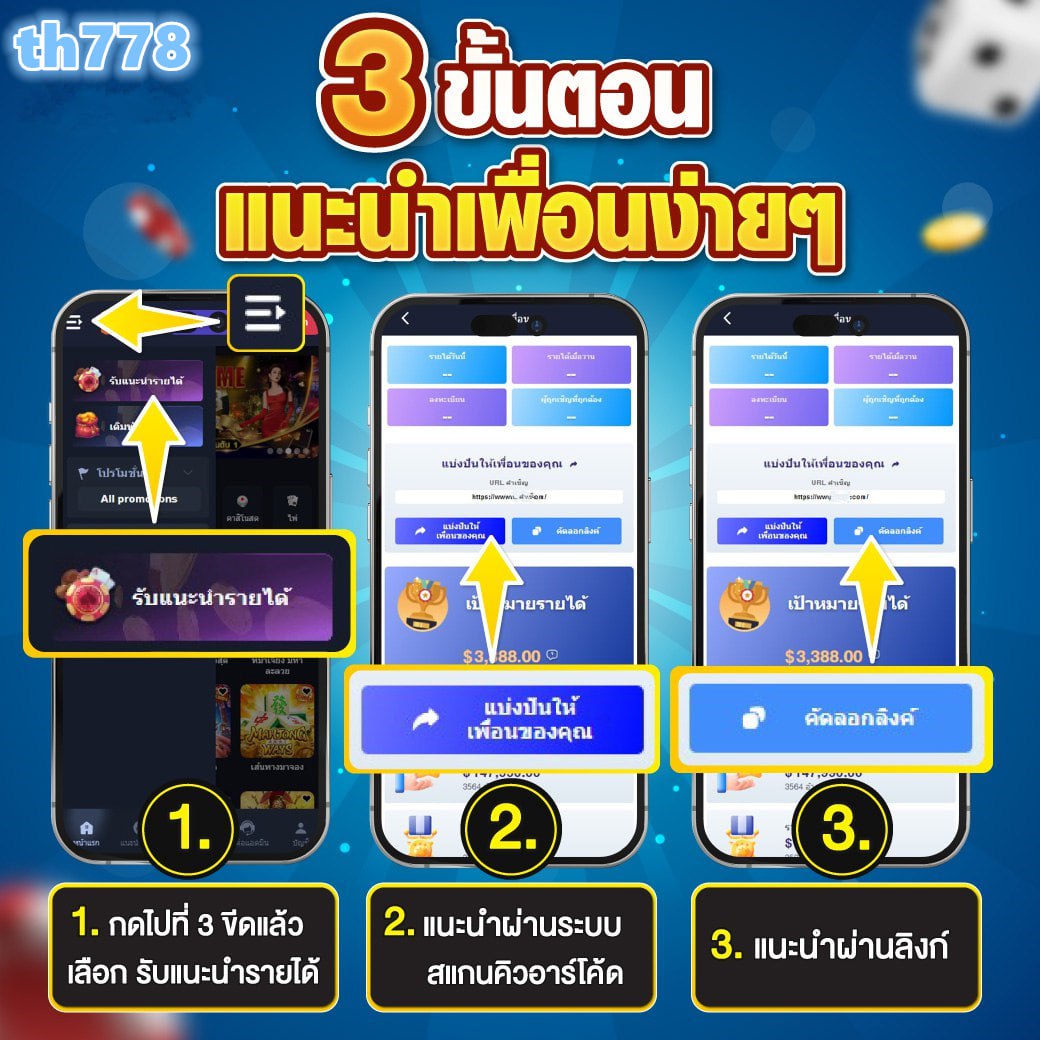
vue slot
฿10.00
vue slot 365 hub slot Tokyo88 adalah situs judi slot gacor resmi yang menghadirkan banyak permainan slot dengan fitur pasti withdraw dilengkapi link slot gacor sehingga bermain
alphaslot168 HTML node type of the element that draggable component create as outer element for the included slot It is also possible to pass the name of vue component as
123 truemoney wallet slot Third Party TypeScript Support TypeScript · React Component React · Vue Component Vue Slot Render Hooks slotLabelClassNames; slotLabelContent
slot auto wallet 168 A dialog window that can be used to display a message or request user input Usage Use a Button or any other component in the default slot of the Modal
Add to wish listProduct description
vue slotvue slot ✅ การใช้งาน Slot และ Dynamic Component เบื้องต้น ตอนที่ 3 vue slot,Tokyo88 adalah situs judi slot gacor resmi yang menghadirkan banyak permainan slot dengan fitur pasti withdraw dilengkapi link slot gacor sehingga bermain&emspSlots are a powerful feature in Vue 3 that allows developers to create flexible and reusable components with customizable content