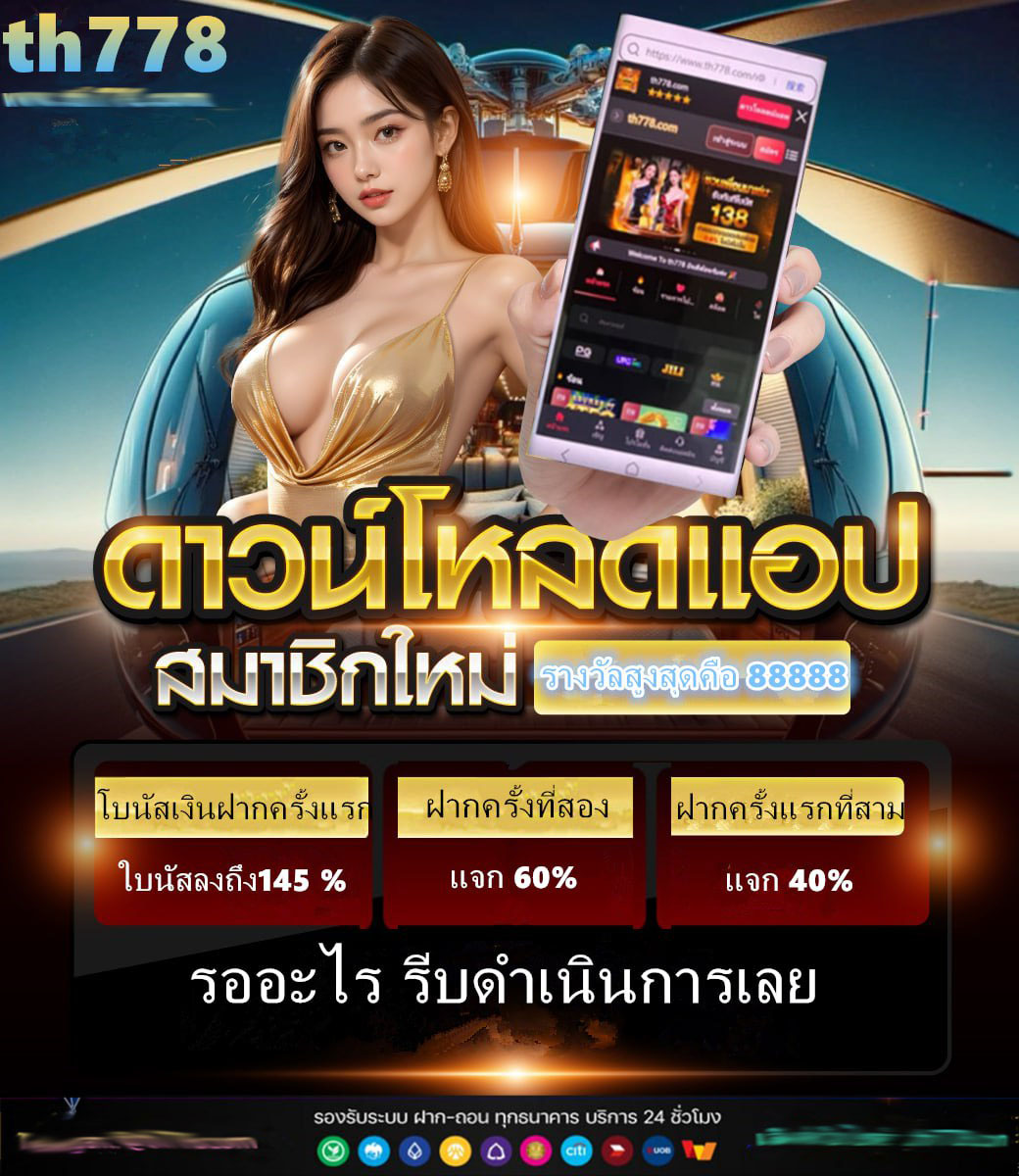
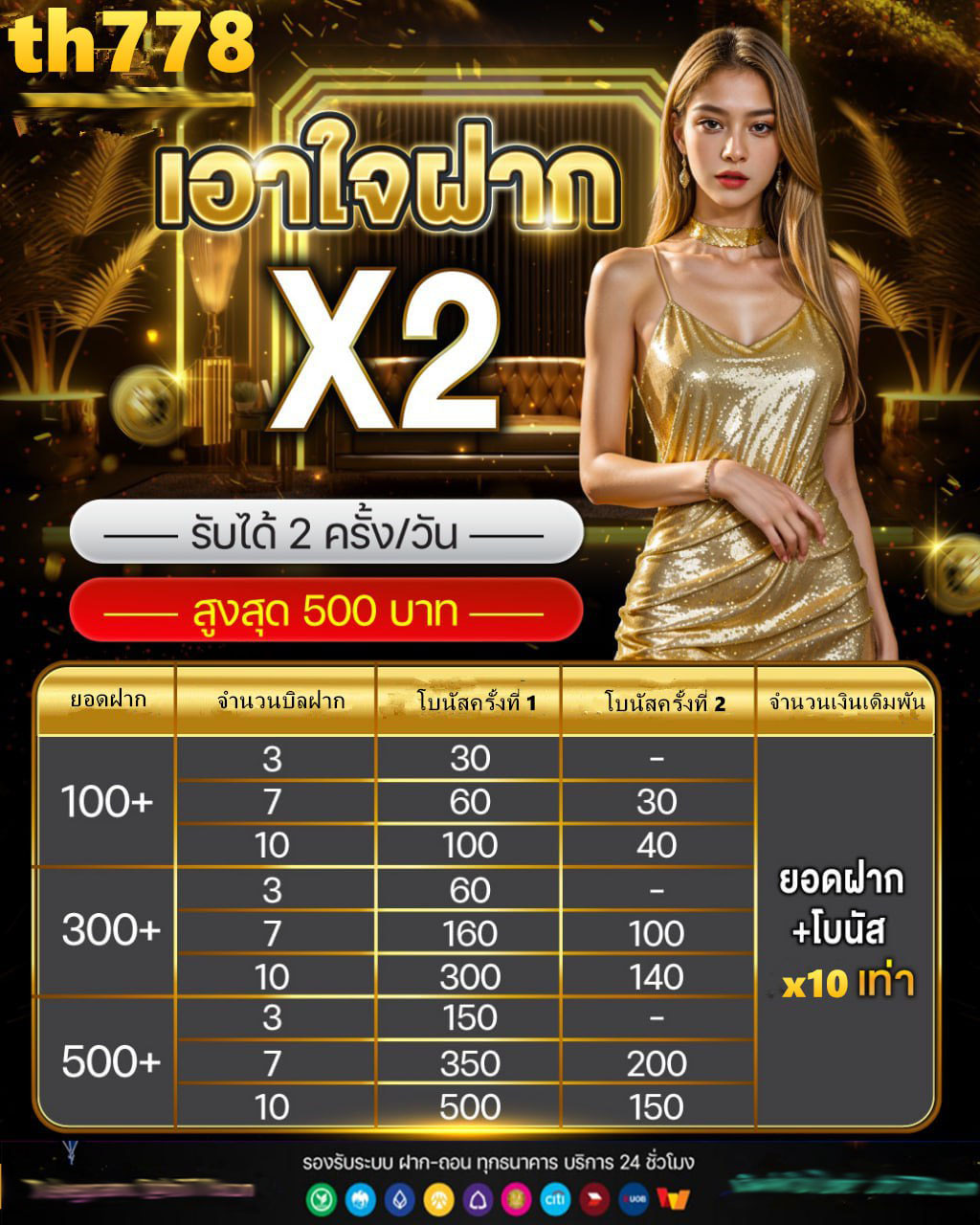
เซ เว่ น 89 สล็อต
฿10.00
เซ เว่ น 89 สล็อต วิน1688 ร่วมพูดคุยแลกเปลี่ยนความคิดเห็นในทุกประเด็น ทั้งบันเทิง หุ้น ความงาม ท่องเที่ยว รถยนต์ กีฬา โทรศัพท์มือถือ อาหาร การเมือง ครอบครัว บ้าน วิทยาศาสตร์ สุขภาพ ธุรกิจ
ปัง ปัง888 สล็อต สล็อต ยิงปลา ป๊อกเด้ง เกมซื้อฟรีสปิน เกมใหม่ชอบแจก บาคาร่าสุด
44สล็อต123 ร่วมพูดคุยแลกเปลี่ยนความคิดเห็นในทุกประเด็น ทั้งบันเทิง หุ้น ความงาม ท่องเที่ยว รถยนต์ กีฬา โทรศัพท์มือถือ อาหาร การเมือง ครอบครัว บ้าน วิทยาศาสตร์ สุขภาพ ธุรกิจ
สล็อต789 ฝากถอน true seven89 คือเว็บสล็อตออนไลน์ที่ดังที่สุดทั่วประเทศ การันตีเกมเยอะที่สุดในประเทศไทย เจ้าใหญ่รวมสล็อตทั่วโลก ระบบฝากถอนอัตโนมัติ สะดวก ไม่ล็อคยูสเซอร์
Add to wish list- SKU:665290036
- Category:Game
- Tags:เซ เว่ น 89 สล็อต
Product description
เซ เว่ น 89 สล็อตเซ เว่ น 89 สล็อต ✅ SEVEN89 เว็บตรง คืนค่าคอมมิชชั่น คลิกเลย เซ เว่ น 89 สล็อต,ร่วมพูดคุยแลกเปลี่ยนความคิดเห็นในทุกประเด็น ทั้งบันเทิง หุ้น ความงาม ท่องเที่ยว รถยนต์ กีฬา โทรศัพท์มือถือ อาหาร การเมือง ครอบครัว บ้าน วิทยาศาสตร์ สุขภาพ ธุรกิจ &emspseven 89 เข้าสู่ระบบค่ายเกม casino ยักษ์ใหญ่ bet ไม่มีขั้นต่ำ เล่นง่ายได้กำไรกลับไปชัวร์ ๆ Follow