i am auto pg plus
฿10.00
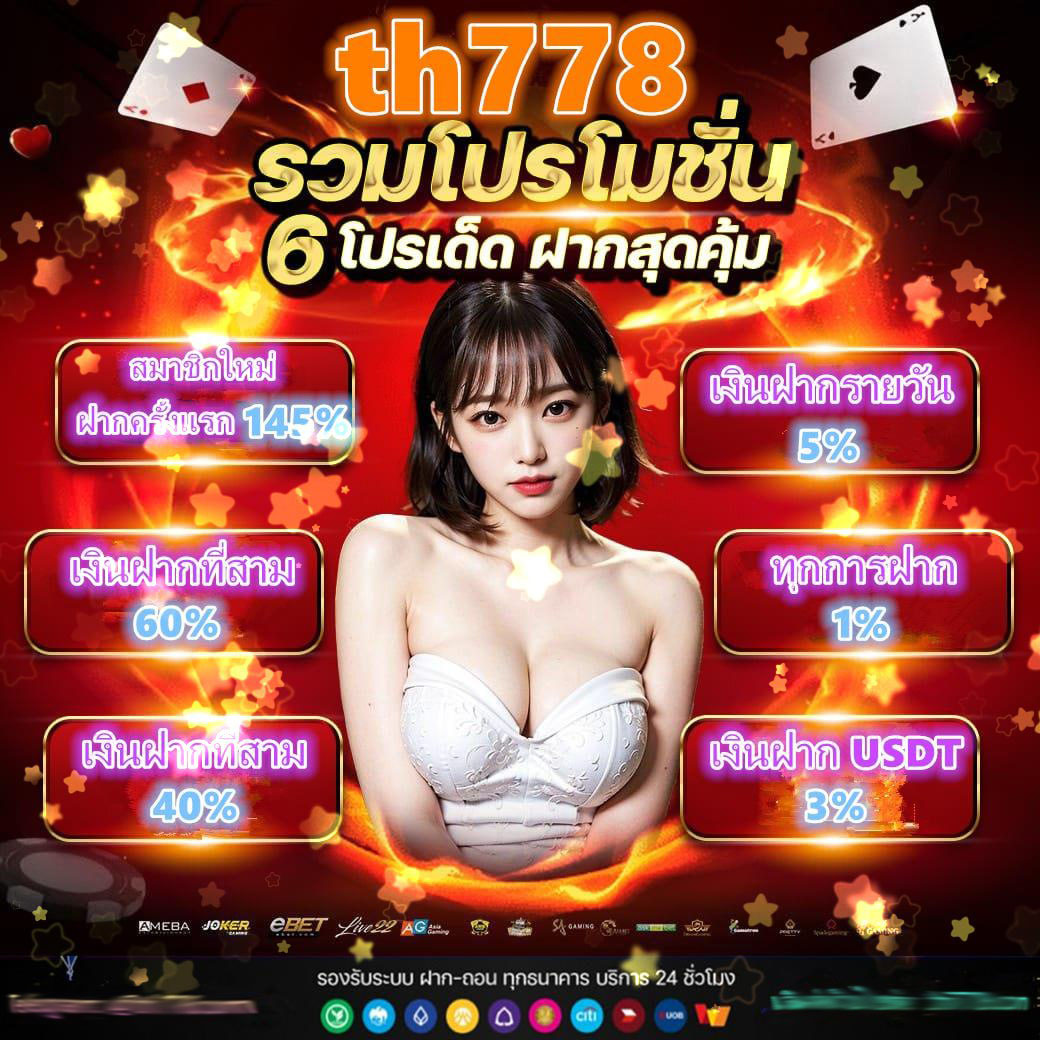
i am auto pg plus sexypgth pg slot เข้าระบบและสำรวจฟีเจอร์ใหม่ล่าสุดในเกมที่คุณชื่นชอบ เรือเสมือนว่าอยู่ในแวดวงคาสิโนเกรดพรีเมียม, พร้อมกับสิทธิพิเศษมากมาย ไม่ว่าจะเป็นของขวัญแต้มสะสม หรือโปรโมชั่นรายสัปดาห์
pg lucky spin สล็อต I AM AUTO สมัครเล่น สล็อตเว็บตรง ครบวงจร รวมสล็อตจากทุกค่ายดัง เช่น สล็อตPG รองรับการฝากถอนผ่าน สล็อตวอเลท เล่นง่าย แตกจริง ปลอดภัย 100%
สล็อต king777 Like New: An item that looks as if it was just taken out of shrink wrap Premium PG Plus Engine Coolant Premix Chemwatch: 32- Version No:
amb44king slot Based on typical findings of noninvasive examinations such as elevated serum NT-proBNP (12,631 pg was eligible for auto-PBSCT after high-dose chemotherapy
Add to wish list- SKU:642671177
- Category:Game
- Tags:i am auto pg plus
Product description
i am auto pg plusi am auto pg plus ✅ สล็อต I AM AUTO สล็อตเว็บตรง สล็อตPG สล็อตวอเลท รวมสล็อตทุกค่าย i am auto pg plus,pg slot เข้าระบบและสำรวจฟีเจอร์ใหม่ล่าสุดในเกมที่คุณชื่นชอบ เรือเสมือนว่าอยู่ในแวดวงคาสิโนเกรดพรีเมียม, พร้อมกับสิทธิพิเศษมากมาย ไม่ว่าจะเป็นของขวัญแต้มสะสม หรือโปรโมชั่นรายสัปดาห์&emspi am askmebet,สล็อต ฝาก 20 รับ 100 ล่าสุด,สเปอร์ส พบ สโมสรฟุตบอลลิเวอร์พูล ไทม์ไลน์ เช็คราคาบอล สล็อตมาใหม่! สมัครสมาชิกฟรี เพิ่มเงินโบนัส 200 บาท