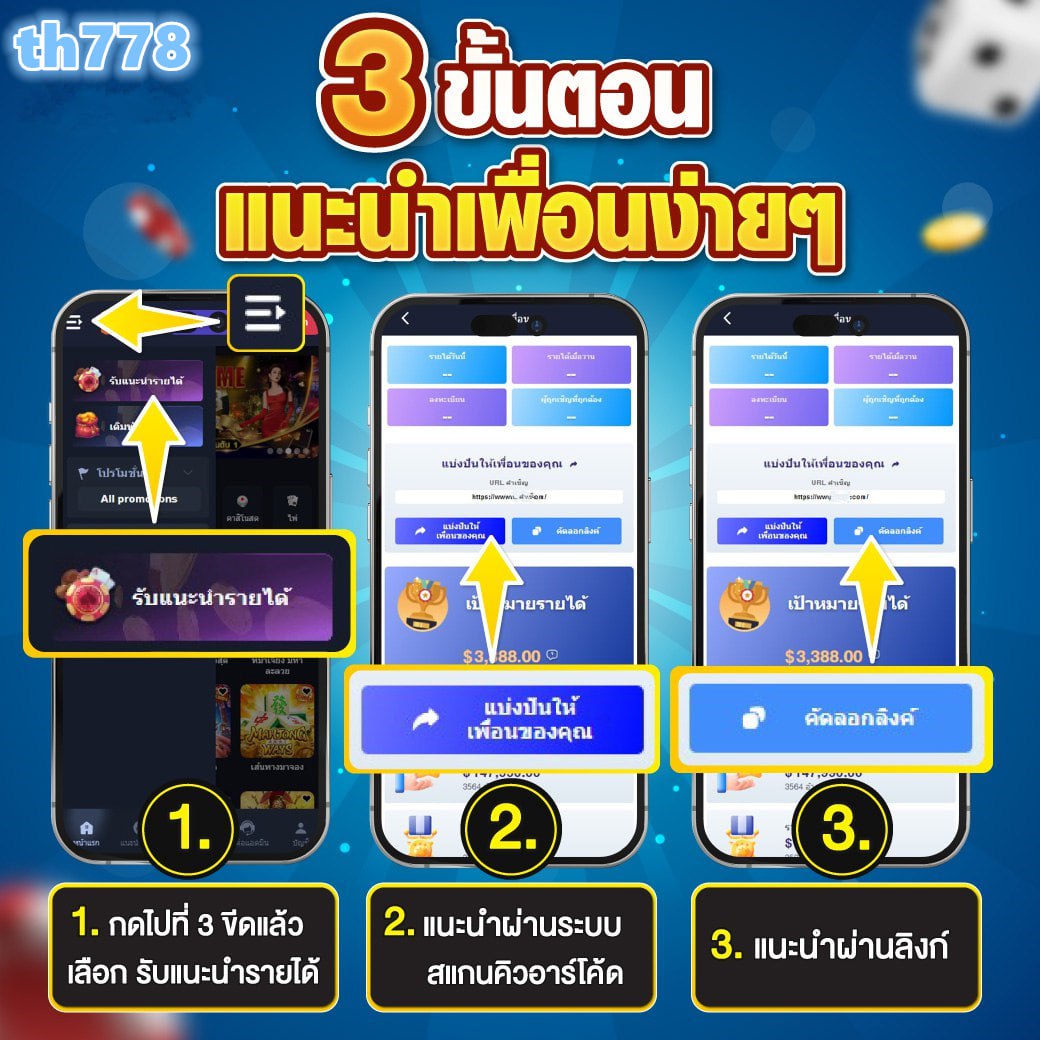
บัส เบท สล็อต
฿10.00
บัส เบท สล็อต th8282สล็อต busbet เป็น เว็บสล็อต ที่ได้รับความนิยมอันดับ 1 ไม่ได้เพราะเพียงแค่เกม ที่มีความสนุกสนานเท่านั้น แต่ยังเป็นเหตุผล ที่นักพนันหลายคน เลือกใช้บริการอย่างต่อเนื่อง เนื่องจากมีการดูแล
mt888 สล็อต สล็อต busbet ออนไลน์ ทางเลือกใหม่ของสายปั่นที่ต้องการความคุ้มค่า เล่นได้ทุกวันไม่มีเบื่อ รวมเกมแตกง่ายในที่เดียว บนระบบที่เสถียร ปลอดภัย ไม่สะดุด
xstar สล็อต สล็อต busbet ออนไลน์ ทางเลือกใหม่ของสายปั่นที่ต้องการความคุ้มค่า เล่นได้ทุกวันไม่มีเบื่อ รวมเกมแตกง่ายในที่เดียว บนระบบที่เสถียร ปลอดภัย ไม่สะดุด
wingสล็อต บัสเบท SLOT ♀️ ใช้เทคนิคการเล่นรูเล็ตแบบมืออาชีพเพื่อเพิ่มโอกาสในการชนะและทำให้การเยี่ยมชมคาสิโนของคุณมีกำไรมากขึ้น ช่วยให้คุณได้รับประโยชน์สูงสุดจากทุกการหมุน
Add to wish list- SKU:672769858
- Category:Game
- Tags:บัส เบท สล็อต
Product description
บัส เบท สล็อตบัส เบท สล็อต ✅ บัส เบท สล็อต สนุกไปกับ ทริปสล็อต เด็ดๆ ได้เงินจัดเต็ม บัส เบท สล็อต,busbet เป็น เว็บสล็อต ที่ได้รับความนิยมอันดับ 1 ไม่ได้เพราะเพียงแค่เกม ที่มีความสนุกสนานเท่านั้น แต่ยังเป็นเหตุผล ที่นักพนันหลายคน เลือกใช้บริการอย่างต่อเนื่อง เนื่องจากมีการดูแล&emspbusbet เป็น เว็บสล็อต ที่ได้รับความนิยมอันดับ 1 ไม่ได้เพราะเพียงแค่เกม ที่มีความสนุกสนานเท่านั้น แต่ยังเป็นเหตุผล ที่นักพนันหลายคน เลือกใช้บริการอย่างต่อเนื่อง เนื่องจากมีการดูแล